How to Start Cybersecurity in 2026
Cybersecurity in 2026
“Intellectual growth should commence at birth and cease only at death.” - Albert Einstein
Cybersecurity is a moving target. As emerging technologies are adopted, the vulnerabilities inherent to them become immediate risks for organizations. Because the field is so vast, it is impossible to create a single “perfect” guide that covers every niche. Instead, I’ve designed this roadmap around the concept of T-shaped skills.
My goal is to help you build a wide, resilient foundation while giving you the framework to dive deep into a specialization; whether that is my own passion for Red Teaming and OS security, or your own path in Defense or GRC. This guide is intended to be a living document, adaptable as you progress from a curious student to a technical professional.
Without further ado, let’s get into it!
The T-Shaped Cybersecurity Professional
The concept of the “Master Generalist” or T-Shaped Skills is something I first encountered via ThePrimeagen. It’s a framework that balances broad knowledge with deep expertise.
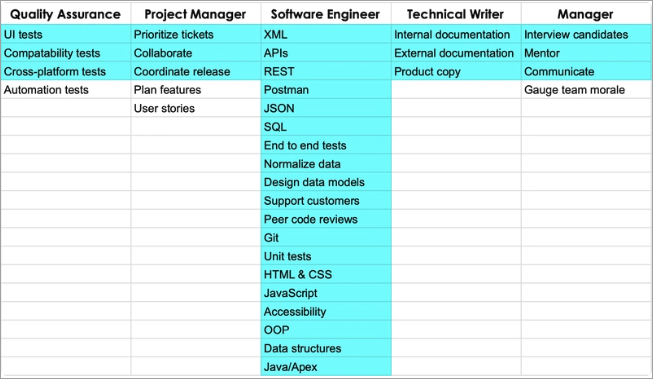
Here is an example of a Software Developer:
Source: DEV
While often used in software engineering, this model is even more critical in cybersecurity. To defend or exploit a system, you must first understand how it functions at every layer. For our field, a solid “horizontal” base includes:
- Networking Basics: Understanding how data moves from point A to point B.
- Operating Systems & CLI: Navigating Linux and Windows environments comfortably.
- Programming & Scripting: Automating tasks and reading code to find flaws.
- Cloud Security: Securing the infrastructure that powers the modern web.
- Incident Response & Threat Analysis: Knowing how to react when things go wrong.
- Cryptography: The mathematical foundation of privacy and integrity.
Specialization: Pushing the Vertical
The “vertical” bar of your T represents your specialization. This is where you go from knowing about a topic to mastering it.
For instance, my goal is to become a Security Researcher specializing in Operating System Security. To achieve this, I have to push my “Operating Systems” and “Programming” bars deeper than the average professional. This involves diving into kernel internals, memory management, and exploitation primitives.
You can even take it a step further; specializing not just in OS security, but specifically in the Linux Kernel.
A word of advice: As you push further down into your specialization, progress slows down and the mental load increases. Take it slow. Document your small wins and build projects along the way to serve as both your portfolio and your motivation.
So where do I actually start?
This is the question I hear most often after discussing the “Master Generalist” mindset. The truth is, the answer is personal and depends entirely on your starting line. Before diving into a course, you need to be honest with yourself about these five areas:
- Networking: Do you understand how data moves, or is “the cloud” still a mystery?
- Operating Systems: Can you navigate a terminal, or are you strictly a GUI user?
- Programming: Do you understand logic and syntax, or have you never written a script?
- Security Theory: Are you familiar with the CIA triad (Confidentiality, Integrity, Availability) and basic threat modeling?
- Mathematics: Where do your logic and discrete math skills currently sit?
While there are dozens of other variables, I am going to assume for the sake of this guide that you are a complete beginner with no idea where to turn.
The Chronological Path
Unlike my previous guides, I want to provide a path based on a blend of my own self-taught journey and the formal curriculum I’ve encountered as a Cybersecurity student at ECPI University. I’ve spent the last year realizing which “rabbit holes” were distractions and which “boring” fundamentals were actually essential.
The following sections are designed to build that “wide base” of your T-shape as efficiently as possible, ensuring you have the context needed to succeed when you eventually decide to specialize.
CompTIA A+
Many in the community wave off the A+ as “too easy,” but that elitist mindset misses the point. This certification provides a critical baseline that is relevant regardless of where you end up in IT. I personally consider it the best starting point because it forces you to understand the intersection of hardware, networking, and security before you ever touch a specialized tool.
Why V15 (220-1201/1202) Matters
The main reason I recommend this now is the major update to Version 15 that launched in early 2025. CompTIA overhauled the material to reflect the modern landscape you’ll actually face:
- Cloud & Virtualization: Enhanced focus on client-side virtualization and cloud models (IaaS, SaaS, PaaS).
- Modern Security: Deep dives into concepts like EDR, IAM, and the ethical use of AI (including addressing LLM hallucinations).
- Networking: Refined coverage of SOHO networks and modern protocols.
- Operating Systems: A shift from legacy Windows towards modern environments, including macOS and Linux.
My Progress & Advice
I passed my Core 1 exam in December 2025 and found that the V15 material is significantly more streamlined than older versions. I’m currently finishing my prep for Core 2 and will be taking it next week; wish me luck!
Pro-Tip: Don’t get stuck in “tutorial hell” with this one. Use resources like Professor Messer to bridge the gap between theory and the Performance-Based Questions (PBQs). As long as you finish both exams in the same series, you’re set.
Cisco Networking Academy
While the CompTIA A+ gives you a broad base, this is where you start building your technical depth. You don’t necessarily need to chase every badge, but if you want a gold standard for your “T-shape,” the Cisco CCNA (Cisco Certified Network Associate) is the way to go.
Defining Your Benchmark
Mastering networking isn’t about memorizing slides; it’s about being able to build. A great personal benchmark (similar to my own Intro to Routing and Switching assessment) is to build a functional enterprise network from scratch:
- The Branch Offices: Configure two routers connecting different buildings with multiple PC endpoints.
- The Data Center: Build a third router connection for a data center using a Spine-and-Leaf architecture with multilayer switches.
- The Edge: Ensure all components have secure access to a simulated ISP “Internet”.
If you can build this, troubleshoot the VLANs, and handle the subnetting, you’ve moved past the “beginner” phase.
Hands-on with Cisco Packet Tracer
For me, the hardest part was moving from theory to application; actually creating the association between a concept like subnetting and a real device. This is where Cisco Packet Tracer becomes your best friend. It’s a free simulation tool that lets you:
- Visualize Traffic: Use Simulation Mode to watch data packets travel across your network.
- Practice Physical Racking: Set up device racks and cables in a 3D-simulated environment.
- Master the CLI: Get comfortable with the Cisco IOS command line without needing expensive hardware.
Where to Start
Where to Start
If you’re looking for a free entry point, start with the Networking Basics course on NetAcad. It’s a 22-hour foundational course that covers everything from IPv4/IPv6 to initial device configuration.
Looking Ahead: Starting February 3, 2026, Cisco is launching a “New Era” for certifications, focusing heavily on AI-ready infrastructure and Network Automation. Even if you don’t take the exam, these are the concepts that will define the industry for the next few years.
Programming and Scripting (Python)
There is often a debate about where to start your programming journey. While some recommend a “web-first” approach (HTML/CSS/JS) or an “old-school” low-level approach (C/C++ or Rust), I believe Python is the definitive starting point for a modern cybersecurity professional.
Why Python in 2026?
Python’s true value lies in its applicability. While low-level languages like C++ or Rust are essential for Malware Analysis or Binary Exploitation, they require a massive time commitment before you can build functional tools. Python, however, allows you to write automation scripts within months.
In the current market, Python has become even more critical due to two major trends:
- The AI Force Multiplier: Most Large Language Models (LLMs) and AI-driven detection systems are developed using Python. Learning Python allows you to integrate LLMs into your workflows to automate threat detection, parse logs, and generate rapid Proof-of-Concepts.
- Security Orchestration: Python is the backbone of modern Security Operations Centers (SOCs). It is used to normalize threat intelligence feeds and automate response tasks in SIEM or SOAR platforms.
Essential Libraries for Your Toolkit
One of the biggest perks of Python is its mature ecosystem of security libraries:
- pwntools: My personal favorite for Capture The Flag (CTF) events and rapid exploit development.
- Scapy: A powerful tool for crafting, sending, and analyzing network packets; essential for network scanning and protocol analysis.
- Requests: Simplifies interacting with APIs and performing web security testing.
- YARA: Used for identifying and classifying malware based on binary or textual patterns.
- Scikit-learn / TensorFlow: Increasingly used for building ML-driven anomaly detection systems.
The Project-Based Learning Path
Regardless of the resource you use (whether it’s the Official Python Website, university courses, or books) consistency is key. I recommend this iterative approach:
- Learn a Concept: (e.g., Loops or Conditional Statements).
- Implement: Write small scripts to solve basic problems.
- Combine: Merge concepts into larger programs, like a basic port scanner or a hash encoder.
- Edge Cases: Consider “negative exemplars”; they are what happens when your script receives unexpected input?.
- Build a Portfolio: Document your journey. Projects like a Keylogger or a Phishing Simulator are excellent ways to prove your hands-on capability to employers in 2026.
CompTIA Security+
You might be wondering why I skipped the Network+ certification when discussing networking. While it’s a fine cert, I believe the CCNA offers significantly more “bang for your buck” in terms of reputation and hands-on technical value.
The Security+, however, is too valuable to ignore. Even if you are pursuing a degree in Cybersecurity, this certification is the global standard for establishing baseline skills in core security functions. It acts as a bridge, taking your technical ability and showing you how to apply it to provide real value to an organization.
Why It’s a Must-Have in 2026
The current version, SY0-701, has shifted away from simple trivia toward proactive risk mitigation and modern infrastructure. It covers critical domains you need to master:
- Security Operations (28%): This is the largest part of the exam, focusing on daily tasks like log review, SIEM monitoring, and incident response.
- Threats, Vulnerabilities, and Mitigations (22%): Understanding malware, social engineering, and how to defend against them.
- Security Architecture (18%): Designing resilient infrastructure using Zero Trust and secure cloud configurations.
- Program Management & Oversight (20%): This is where you learn the “corporate” side; governance, risk management, and compliance (GRC).
Beyond the “Corporate Slop”
While terms like the CIA Triad or Governance might feel like theoretical filler, they are the level of awareness required to understand an organization’s needs. Thanks to platforms like TryHackMe, I’ve already been able to dive into:
- The Pyramid of Pain: Understanding which indicators are hardest for adversaries to change.
- The Diamond Model: A framework for analyzing individual cyber events.
- TTPs (Tactics, Techniques, and Procedures): Shifting the focus from simple file hashes to actual attacker behavior.
Study Resources
If you are looking for the gold standard of preparation, look no further than Professor Messer. His free SY0-701 video course covers all 121 topics in detail, and he offers excellent practice exams and course notes that are frequently updated.
Note: I have an upcoming “Advanced Cybersecurity” class that covers this material, but I’m already using these resources to get ahead. In 2026, being “ready” for the job means having both the degree and the industry-standard certs to back it up.
For those interested in Offensive Security
If you are interested in OffSec, you have a plethora of resources to pick from. I actually wrote a comparative analysis paper where I compared TryHackMe vs HackTheBox using learning science frameworks. My conclusion? TryHackMe is the perfect guided entry point for those with a pure curiosity for the field. However, to push past that intermediate “ceiling,” HackTheBox (HTB) offers the most long-term value.
Why HackTheBox for 2026?
The real value of HTB isn’t just the competitive ranking; it’s the ProLabs. These aren’t just single-machine challenges; they are entire simulated enterprise networks (like Offshore or Zephyr) that require you to pivot through multiple subnets and compromise Active Directory environments. This experience is critical for transitioning from a “get root” CTF mindset to real-world penetration testing.
The Certification Landscape: CPTS vs. OSCP
The HTB Certified Penetration Testing Specialist (CPTS) has rapidly become a favorite for those who value depth over just “HR filters”. It is widely considered to be on equal footing with (and technically more exhaustive than) the legendary OSCP.
Both certifications share a high-intensity, practical DNA:
- Hands-on Exams: No multiple-choice; you have to break into a network to pass.
- Comprehensive Reporting: You must document your findings in a commercial-grade report.
- Real-World Scenarios: Focus on Active Directory, lateral movement, and vulnerability chaining.
My Strategy
While the OSCP remains the gold standard for HR recognition, its high cost (~$1,700+) makes it a significant investment. My plan is to conquer the CPTS first this year. At a fraction of the cost (especially with a student subscription) it provides a more modern and technically deep curriculum.
Goal: I intend to use the CPTS to solidify my expertise and land a junior role, then pursue the OSCP once I have employer backing. As you push deeper into offensive security, remember: it’s not about how many flags you catch, but how well you can communicate the risk back to the organization.
For those interested in Defensive Security
Admittedly, this is the area I have spent the least amount of time researching. However, a “Master Generalist” cannot ignore the blue team. To be a better attacker, you must understand how defenders think, and to be a great defender, you must understand the infrastructure you are protecting.
Recommended Platforms
Based on my research and limited hands-on experience, here are the platforms that currently define the defensive landscape:
- Let’s Defend: Now part of the HackTheBox ecosystem, this is a SOC (Security Operations Center) simulation platform. It allows you to investigate realistic alerts, analyze logs, and handle incidents in a simulated environment.
- TryHackMe: As I’ve mentioned, their Blue Team paths are excellent. They provided me with a solid understanding of the “defender’s duties” by teaching the fundamentals of digital forensics, SIEM (Security Information and Event Management), and log analysis.
- CyberDefenders: Often cited as the “HackTheBox of Blue Teaming,” this platform is great for pushing past the basics with complex labs involving disk and memory forensics.
Honorable Mentions
If you want to explore further, these platforms are highly regarded in the community for building practical defensive skills:
The Defensive Foundation: System Hardening
Even if you aren’t using a dedicated platform, you are likely already building blue team skills if you manage your own systems. In my own journey (specifically while hardening my Ubuntu and Arch Linux environments) I’ve found that true defense starts with:
- The Principle of Least Privilege: Ensuring users and services only have the access they absolutely need.
- Network Configuration: Managing firewalls and monitoring traffic to detect anomalies.
- Log Management: Understanding how to read and interpret system logs to identify potential breaches.
When will we ever use that in the real world?
I’m sure you’ve heard this question asked in a math class. Math beyond Algebra might seem like “academic fluff” to most, but for a Cybersecurity Professional, it is the bedrock of the field.
I realized this firsthand during my first professional-level CTF: UTCTF 2025. The Cryptography challenges were unlike anything I had ever seen. Despite knowing how to code and prompting GPT for what felt like an eternity, I couldn’t even start them. The issue wasn’t my programming; it was my lack of mathematical fluency. I realized I didn’t know the first thing about modular arithmetic, number theory, or discrete math. It was a humbling experience that made me realize how much further I needed to push my “T-shape” in this direction.
The Path to Mathematical Fluency
To avoid that “out of my league” feeling, you need to build a foundation in Discrete Mathematics. This isn’t just about memorizing formulas, it’s about understanding the logic of finite systems. Since I’m a student on a budget, I’ve been focusing on these high-quality free resources to bridge the gap:
- Discrete Mathematics: An Open Introduction: This is a fully free, open-source textbook. It covers the logic, set theory, and number theory foundations that are the “why” behind every encryption algorithm. It’s been my go-to for clearing up the confusion I felt during the CTF.
- Khan Academy (Cryptography): If you need to start from absolute zero, this is the place. Their series on modular arithmetic and the Diffie-Hellman key exchange is world-class and perfect for building that initial intuition.
Bridging Theory and Code
Once you have the basics, you need to apply them. As a security researcher, your goal is to translate these mathematical proofs into Python scripts.
- CryptoHack: This is easily my favorite resource for this. It’s a gamified platform that teaches you cryptography by making you break it. You’ll use Python to solve challenges involving RSA, AES, and Elliptic Curves. It forces you to actually implement things like the Extended Euclidean Algorithm rather than just reading about them.
- Cryptopals: These are the legendary “Matasano” challenges. There is no hand-holding here. You simply use your programming skills to build and then exploit real cryptographic systems. It’s one of the best ways to gain a “gut feeling” for how these systems fail.
My Strategy: The Targeted Approach
Don’t feel like you need to become a mathematician overnight. Instead, I’ve been using a targeted research approach that fits into my project-based learning style:
- Encounter a Challenge: Find a crypto problem on a platform like picoCTF or a past CTF.
- Identify the Gap: If you see a term you don’t recognize (like “Modular Inverse” or “Euler’s Totient”), look it up in the discrete math book.
- Script it: Write a Python function to solve that specific math problem.
- Repeat: This is how you build that depth without getting overwhelmed.
By the time the you get to your own CTF and face a cryptography challenge, you won’t be staring at a blank screen; you’ll be writing the exploit.
Does it ever stop?
The short answer is: No. It never stops.
I included this section because I often meet people who stumble into cybersecurity solely to “make money.” While the career is rewarding, that shouldn’t be your only driver. Cybersecurity is as vast and vital as medicine. You wouldn’t trust a doctor who stopped reading medical journals the day they got their license; similarly, a security professional must remain a student for life to keep up with every new breakthrough and vulnerability.
The 2026 Landscape: Adaptation is Survival
We are currently seeing a massive shift with the rise of LLMs and AI Security. This isn’t just a trend; it’s a fundamental change in how we attack and defend systems. It presents a massive opportunity, but it requires a willingness to adapt and an obsessive hunger for knowledge.
The Reward
Personally, I wouldn’t want it to be any other way. There is a specific, irreplaceable feeling that comes with learning a complex new concept (like memory safety or kernel exploitation) and finally seeing it work in a real-world scenario. That “lightbulb moment” is why I wake up every day happy to have chosen this path.
Thank you for reading through this guide. I hope it helps you build a resilient foundation for your own journey. Remember: see the world differently, stay consistent, and never stop asking ‘what if.’
Until next time, stay safe and happy hacking!


